Is Your Identity Authentication Solution a Liability or a Competitive Advantage?
Biometric MFA processes bolster security and enhance UX
Some of today’s most common authenticators, like One-Time Passwords (OTPs), smart cards, and USB tokens, are failing to provide the level of security that organizations dealing with highly sensitive data require to keep their IAM (Identity and Access Management) systems and customers safe – even when these factors are used in conjunction as part of an MFA (Multi-Factor Authentication) strategy.
Industries like financial services, healthcare, and telecom, especially, need to implement the most secure, user-friendly identity authentication solutions available on the market. Gartner’s most recent report, Innovation Insight for Many Flavors of Authentication Token, clearly outlines how “legacy” MFA factors are no longer viable when it comes to delivering either security OR user experience: “Authentication tokens provide the commonest way of implementing MFA to address the weaknesses of passwords and reduce ATO risk, but token-based methods are increasingly defeated. Security and risk management leaders must act swiftly to mitigate risks and plan for migration to phishing-resistant MFA.”
3 Types of MFA Authenticators
In the age of AI (Artificial Intelligence) and rampant phishing, identity fraud and the fraudsters who commit cybercrimes are increasing in both incidence and sophistication, respectively. Combatting identity crimes is a battle best waged using MFA. The concept behind Multi-Factor Authentication (MFA) is simple: rather than requiring a single, less-secure form of authentication (like a password), MFA layers multiple authentication steps together, like a PIN plus a facial scan. By using more than one simple authentication method, a stronger, synergistic form of security is created.
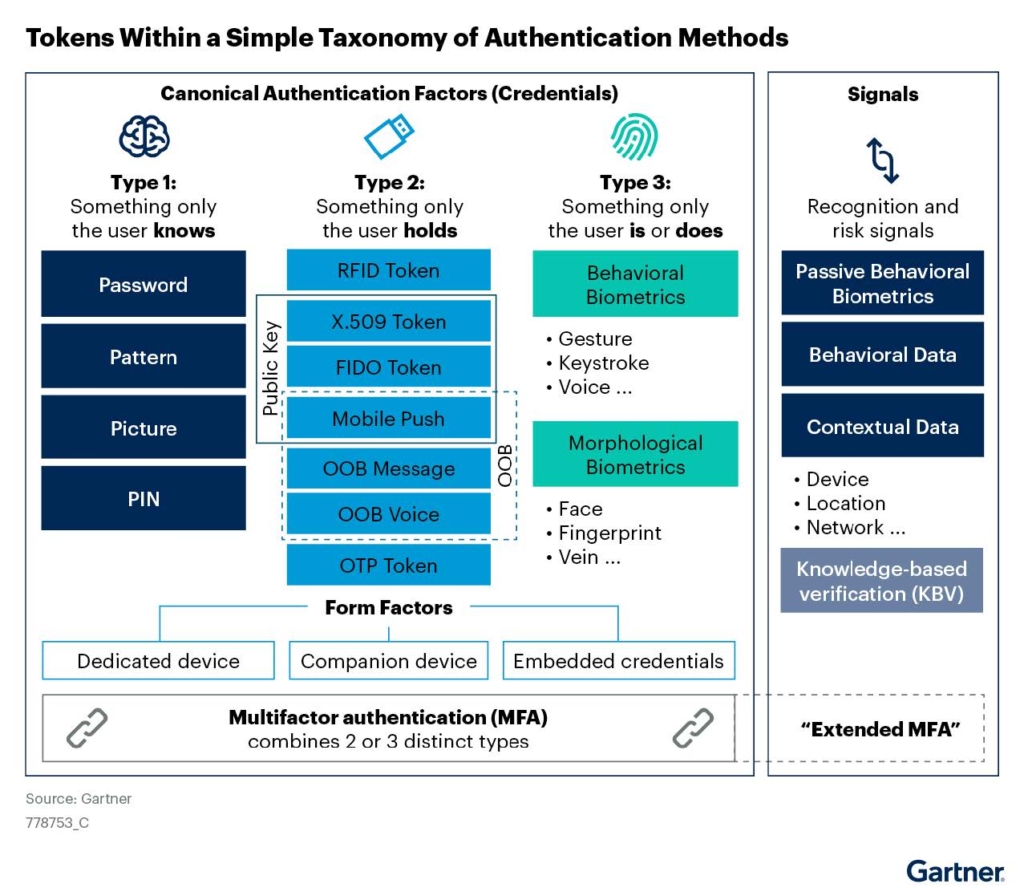
The three categories of authentication factors, according to Gartner, include:
Type 1 Authentication Factors
Also known as Knowledge-Based Authentication (KBA), type 1 factors are frequently phished, breached, or hacked; cybercriminals, often, will then sell stolen credentials on the dark web. Type 1 factors are the weakest form of authentication possible. Consequently, type 1 factors are not typically – or at least should not be – used for transactions of consequence (like financial or healthcare transactions) without the addition of a secondary factor (type) of authentication. Adding another factor is what constitutes an MFA approach. A common example of MFA that many users are familiar with is a password (KBA) plus an OTP (type 2 – see below).
Type 2 Authentication Factors
Type 2 authentication factors are “something the user has,” also known as possession-based (or token-based) authentication. This category includes factors like a user’s device (smartphone, tablet, laptop, etc.), something sent to that device that is dependent upon the possession of that device (OTP), or a token, like a USB drive or smart card. Gartner specifically highlights how these specific authentication tokens are failing to provide enough security: “One-Time Password (OTP) hardware tokens, and especially phone-as-a-token methods, dominate many Multi-Factor Authentication (MFA) use cases, but these methods are increasingly defeated by phishing (broadly defined) and other attacks.”
Type 2 authenticators – similar to type 1 – are also considered “legacy” factors, meaning they have been around and widely used for quite some time. These factors are especially at risk for being lost, misplaced, or stolen. As any forgetful person with a smartphone knows, the weekly search for your “lost” phone (one that usually ends with your hand between the couch cushions) can be stressful enough as it is. And that stress is compounded when you think about how many transactions rely on possession of your device and the potential consequences of not being able to access that device – or worse, the wrong person having access – for an extended period of time. That’s why most organizations choose a combination of factors (MFA) that includes something that is possessed and something that is either known or is a physical (biometric) factor.
Type 3 Authentication Factors
Something a user is (their face, fingerprint, or voice) or something the user does (behavioral biometrics, like keystroke, gait, or typing speed) comprise type 3 authenticators. As the chart from Gartner’s Innovation Insight for Many Flavors of Authentication Token shows below, biometric authentication factors are the most secure and most user-friendly authenticators.
Type 3 factors have the added benefit, unlike type 1 or 2 factors, of being impervious to phishing, stealing, or loss. Biometric factors create a stronger type of MFA; a popular biometric approach to authentication includes Face ID (native to many smartphones) plus a password – a widely used approach for banking app logins, for example.
AI and machine-learning technology is continually being used to optimize facial recognition matching engines. But fraudsters are ever-present, waiting in the wings to use digital or analog versions of real people to exploit the weaknesses of all types of authentication. To better fight identity fraud, facial recognition technology scientists developed groundbreaking fraud detection technology, called Passive Liveness Detection (PAD). This type of liveness detection was made possible with advancements in artificial intelligence and the widespread availability of high-quality yet inexpensive cameras. Most smartphones that have been in production since 2010, for example, have cameras that can perform facial scans.
PAD can detect if fraudsters try to use photos, cutouts, masks, videos, or recordings of an authorized user in an attempt to spoof a facial or voice biometric system – and this layer of security all happens in the background, without any input or additional actions (hence, “passive”) required of the user.
UX vs. Security: Do You Really Have to Choose?
Another important consideration covered by Gartner in their report pertains to friction during the authentication process: “Customer MFA (“strong customer authentication”) is complicated by the range and diversity of customers, the varied penetration of enabling technologies (such as smartphones and passkeys), and high-friction enrollment processes.”
Legacy factors, as mentioned above, are the most friction-filled factors, as they imply a “knowledge burden” to be placed on the user; remembering hundreds of different passwords or security questions, like your best friend’s birthday or mother’s maiden name, for example, can become tedious and difficult to manage, especially as more than one-third of people have over 20 passwords. Consumers have also become fed up with passwords. A recent study by Daon showed that passwords are the most used, yet least trusted, security measure of consumers in the U.S. and UK.
One way to remove as much friction as possible from the authentication process for users is to employ type 2 or 3 identity factors, ideally in combination as an MFA strategy. Possession and biometric-based identity authentication factors both allow users to “come as they are” and defeat the burden of knowledge from digital identity journeys. Type 2 and 3 authentication factors can help organizations maintain robust security while ensuring users can access accounts and data with just a simple face scan or OTP instantly sent to them via SMS.
Have it Both Ways
Daon offers the widest portfolio of Type 1, 2, and 3 authentication factors recommended by Gartner on the market today through our next-gen MFA product, xAuth™. xAuth is a truly compatible, flexible solution that allows organizations to choose what’s best for them – and not settle for a one-size-fits-all solution. With Daon xAuth, you’ll get advanced security trusted by hundreds of thousands of users across six continents, simple, reliable UX, and choices when it comes to how your users can authenticate themselves.
With over 200 patents under their belt, our team of scientists has been developing and optimizing the machine-learning algorithms that power our biometric authentication solutions for over 20 years. Our anti-spoofing technology leads the industry in efficacy and reliability – it can even detect AI-driven voice recordings or facial scan spoofs and a wide range of digitally manufactured identities, ensuring your CIAM and your customers are always safe.
To learn more about xAuth or to see it in action, contact one of our product experts today.
To read your complimentary copy of the full Gartner report, click here.








