What the Media Gets Wrong About Deepfakes and iPhone Injection Attacks
Let’s say a banking customer opens their mobile app to transfer funds and holds their phone up for facial verification. The authentication succeeds, granting instant access to move money. Just another routine transaction complete, but this time the person holding the phone isn’t the account holder at all. Malicious code intercepts the video stream, feeding the app synthetic pixels of the real customer’s face while a fraudster operates the account undetected. Is a scenario like this really possible?
Recent headlines have cautioned that a “new hacker tool can inject AI-generated deepfakes right into your iPhone.” This claim is based on a proof-of-concept experiment conducted on jailbroken iOS devices. Because the built-in platform protections have been removed, attackers can commandeer the camera feed and deliver synthetic video to an app while the camera preview appears normal to the user. This is what’s called a digital injection attack, an attack vector where the pixels received by your application did not originate from the physical camera sensor.
Conventional presentation attacks are distinct from digital injection attacks. Presentation attacks attempt to deceive the lens by displaying a masked disguise, a printed photo, or a replay on a screen. Digital injection attacks attempt to deceive the ‘wire’ by inserting or rerouting frames within the capture pipeline following the lens. This distinction is significant because the defenses are not identical, despite the fact that they do somewhat overlap. For example, both attack types must defeat liveness checks. It is possible to pass a fundamental ‘is the face moving’ liveness check with either method; however, your application may still be vulnerable to injection attacks if it accepts pixels that were not produced by the actual sensor.
So why does the injection attack technique being discussed only work on jailbroken phones? Platform posture is a control in and of itself. Upon jailbreaking or rooting a device, the trust boundary is breached, allowing attackers to impersonate devices, hook frameworks, and circumvent standard checks. This does not imply that the iOS camera APIs are “broken;” rather, it indicates that the operating system’s integrity guarantees are no longer valid. Before the capture process commences, secure mobile identity systems identify compromised environments as high-risk and either require step-up authentication or deny access.
Digital injection attacks aren’t limited to this one example. While jailbroken and rooted devices represent the easiest targets due to compromised platform integrity, injection attacks can also succeed on non-jailbroken phones through other vectors. Variants of digital injection attacks are present on rooted Androids, desktops via virtual webcams, and through man-in-the-app triggers that are situated between the camera and the application. Adversaries are incentivized to deploy injection attacks in areas where device integrity is weakest. Deepfakes are already being used in a variety of fraud schemes, including image-based exploitation, fake video interviews, and a broad wave of consumer scams.
Building Layered Defenses Against Digital Injection Attacks
Protecting against digital injection attacks requires layered controls working in concert, not a single detection algorithm. Effective defenses include:
- Device Integrity and Attestation: Identify jailbreaks, hooking frameworks, and suspicious origins. Decline to proceed or require supervised verification when risks are detected.
- Sensor Binding: Bind the capture session to the genuine camera sensor and reject virtual or loopback sources. If your system cannot differentiate between a physical sensor and synthetic input, you’ve left the door open.
- Dynamic Challenge-Response: Incorporate unpredictable, per-session micro-kinematic and photometric stimuli with strict time constraints that are challenging to replicate through a hijacked pipeline.
- Pipeline Security: Implement mutually authenticated TLS with certificate pinning, per-frame nonces, and sequence/timestamp attestation to distinguish buffered or rendered streams as out-of-profile.
- Server-Side Signal Analysis: Analyze signals holistically, including illumination consistency, blink trajectories, parallax and rolling-shutter artifacts, and reconciliation of device state against challenge responses.
- Adaptive Response: Step up to supervised verification when anomalies accumulate, rate-limit retries, and curtail suspicious sessions.
When it comes to thwarting complex digital injection attacks, technical controls alone are insufficient without proper governance frameworks to validate their effectiveness. Buyers should demand independent validation that encompasses injection, rather than focusing only on traditional presentation assaults. The Face Verification Certification program of the FIDO Alliance explicitly addresses deepfakes, liveness, bias, biometric matching, and injection assaults, providing procurement teams with a method to transition from vendor claims to independently verified outcomes. It is also critical to ensure that your controls are mapped to NIST’s Digital Identity Guidelines. This will enable auditors to confirm that your risk-based decisions are in accordance with the established standards for authentication integrity and remote verification.
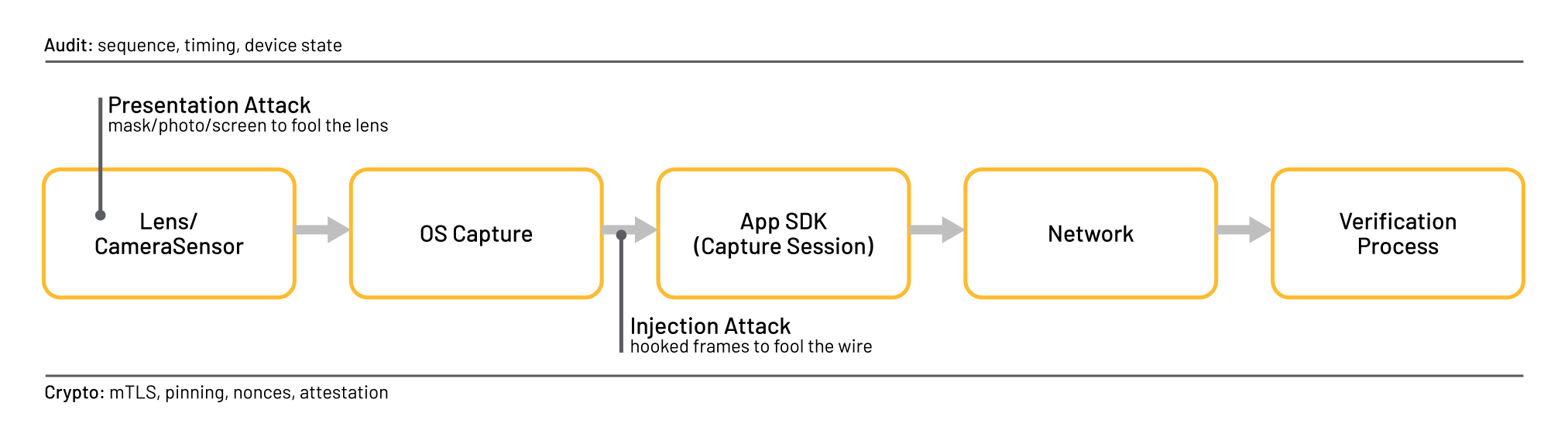
Figure 1. Presentation vs. Injection: where each attack acts on the pipeline (Source: x.com Grok).
These technical controls establish what to defend against, but converting defense into operational outcomes requires platform capabilities that measure effectiveness, enable learning, and drive continuous improvement.
The Operational Layer: Making Defense Against Digital Injection Attacks Actionable
Instrumentation converts defense mechanisms into measurable outcomes and operational improvements. Beyond deploying layered controls, organizations need platform capabilities that transform detection signals into fraud reduction while maintaining seamless experiences for legitimate users. Essential instrumentation capabilities include:
- Fraud Indicator API: Enables customers to flag fraudulent process instances directly when discovered. This creates a clean signal visible in the back office that gradually becomes the core of a learning cycle, connecting confirmed fraud to session data, including device posture, challenge responses, and transport signals. That feedback refines thresholds, adapts step-up policies, and establishes quarterly reporting on verified cases rather than anecdotes.
- Case Management: Transforms isolated fraud incidents into actionable patterns. Investigators can initiate cases, attach relevant process instances, search across demographic and biometric pivots, and annotate findings. Process instances can be incorporated into cases to preserve context, whether during live user journeys or from back-office analysis. This converts “interesting signals” into prosecutable narratives and provides product owners with a clear understanding of what policies actually prevent.
- Device Intelligence: Makes environmental risks visible and actionable. Since digital injection attacks thrive in compromised environments, device intelligence gathers posture and telemetry data to customize journeys based on risk. Signals include VPN and TOR usage, Android root and iOS jailbroken status, and web developer tools availability. Customers can export raw fields into their own analytics, construct checks as journey activities, and step up or fail closed when necessary. This decreases false positives in clean environments while increasing confident interventions in hostile ones.
- Watch Lists: Help teams track repeat offenders, recycled devices, and reused document numbers. Customers can flag devices, IP addresses, document numbers, and similar identifiers as potentially hazardous, maintain list accuracy, and assess them in real time during journeys. Trusted users proceed smoothly while known bad actors encounter immediate blocks.
These capabilities work together because digital injection encompasses multiple attack strategies designed to substitute pixels and obscure their origin. Effective defense requires systems that bind capture to physical sensors, validate sequence and timing, respond immediately to integrity failures, and learn from confirmed fraud cases. Each instrumentation component plays a distinct role: the Fraud Indicator API enables continuous learning, Case Management helps investigators identify patterns, Device Intelligence supports confident risk-based decisions, and Watch Lists ensure past threats don’t resurface.
This integrated approach drives measurable business outcomes: reduced fraud losses quarter over quarter, faster verification times for legitimate users, and higher digital injection attack detection rates at established thresholds. Verification speed is measured at both median (p50) and 95th percentile (p95), capturing how fast the process typically feels and how bad the worst cases get.
Strategic Imperatives for Injection Attack Defense
Digital injection attacks represent an evolution in identity fraud that demands equivalent defenses. While headlines about “deepfakes on your iPhone” may sound alarming, the reality is more nuanced: these attacks target the weakest points in device integrity but can be effectively defended against with proper controls. Organizations that understand this distinction can deploy targeted defenses rather than reacting to sensationalized threats.
The best way forward requires organizations to move beyond single-point solutions toward integrated defense systems. Layered technical controls must be paired with governance frameworks that validate effectiveness, instrumentation platforms that transform detection into learning, and independent certification that provides procurement teams with confidence. Organizations that bind capture to physical sensors, validate device integrity, analyze behavioral signals holistically, and continuously refine their models based on confirmed fraud will establish resilient defenses against injection attacks.
Ultimately, the goal is not perfection but measurable improvement: reduced fraud losses, faster verification for legitimate users, and higher catch rates for attacks. As digital injection attack techniques continue to evolve, the organizations that invest in comprehensive detection, validation, and learning systems today will be ideally positioned to adapt to tomorrow’s threats.









