Hacking the SEC: How Passwordless Security and 3rd Party Due Diligence Can Mean the Difference Between Safety and Scrutiny
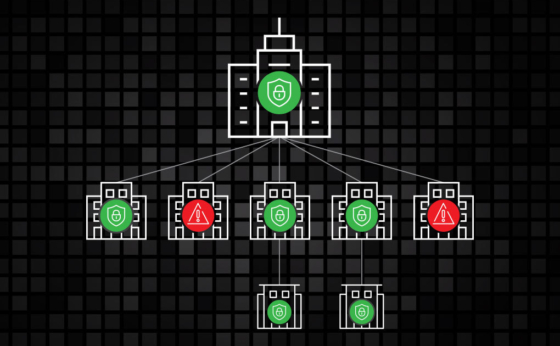
Greater vigilance over authentication protocols and passwordless, biometric security is needed amidst today’s threat landscape.